Today, most companies face the problem of confidential information leaking outside the organization’s perimeter. Increasingly, this is due to employees’ careless communication with artificial intelligence. People tend to use this technology only as a tool that facilitates their routine tasks, completely forgetting about data security and confidentiality.
And we have a question: Is the business ready to risk everything for the sake of the trend and the desire to optimize everything?
We have prepared an article where Oleksandr Skrypnyk, Sales Engineer at BAKOTECH, uses the example of vendor Skyhigh Security to show how to protect yourself from the risks associated with using AI.
How do users themselves provide data to language models?
It is not even necessary to resort to hacking systems to lose control over data today. Users themselves provide sensitive data to language models without thinking about the potential consequences.
For example, the most common use case for AI is sending a file to get a brief description of its contents. But the user does not consider one point: the file may contain confidential information. It turns out that the AI generates an answer to the question about the file’s content, but all the information remains and is used as material for training the language model.
If we mention the big players (OpenAI, Microsoft, X), they can partially guarantee data security, but “partially” does not mean “fully.” And in information security, it is always necessary to stay one step ahead to ensure protection.
Let’s imagine that the organization has a policy that regulates services approved by the Information Security department. This list includes Gemini as a tool that can be used by company employees. This is how Skyhigh Security solutions work. The vendor has several control options when using these services. We will consider two of them that contain DLP (Data Loss Prevention) functionality: SWG (Secure Web Gateway) and PA (Privilege Access).
SWG (Secure Web Gateway)
A classic proxy server that passes traffic through itself and performs control based on policies created by the solution administrator. Skyhigh Security monitors market trends and understands the risks of using AI resources. To achieve this, the vendor has added a set of rules that can implement full protection using artificial intelligence right from the start.
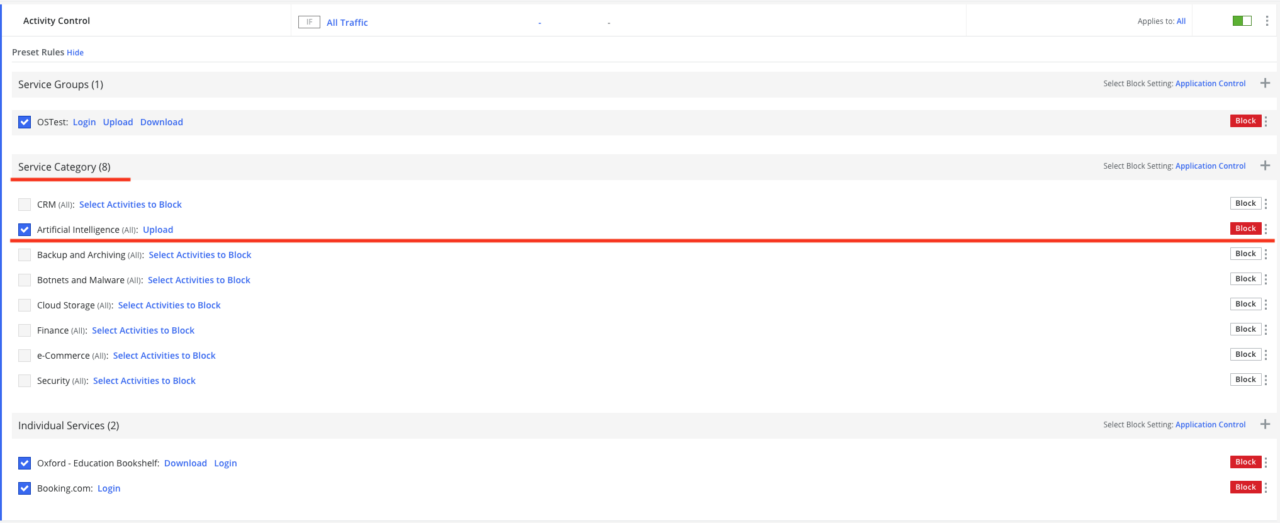
Let’s consider the item Service Category with service classification. We are interested in artificial intelligence — in our case, we have chosen to block the export of any information. You can also select other user actions, and they will also be controlled.
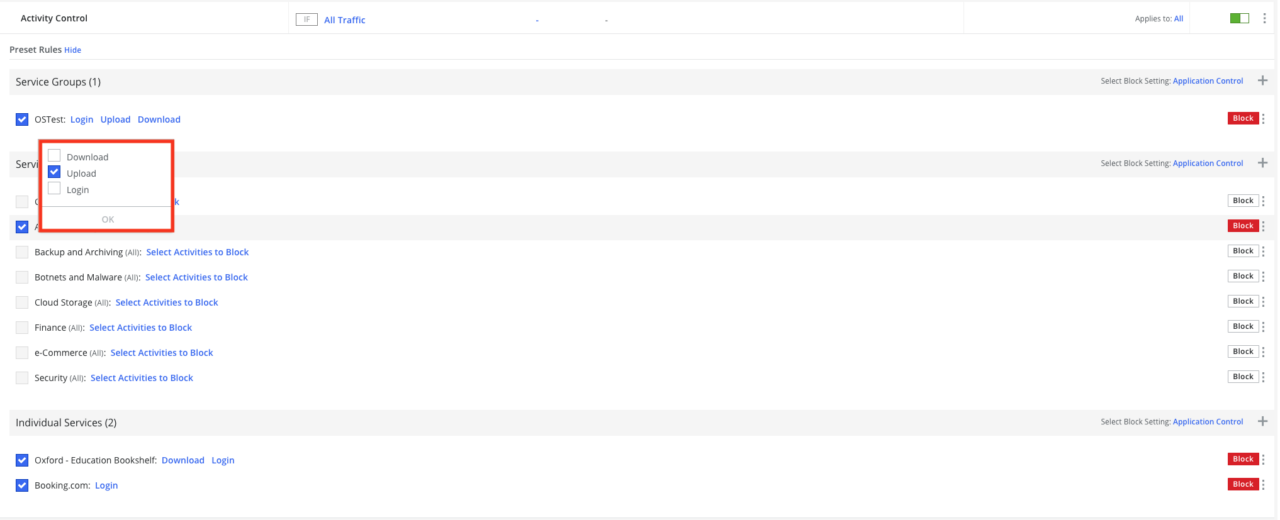
And what if we need to control a particular service?
This can be done by adding personal services (Individual Service) from the drop-down list. We independently select the service for which security measures should be taken.
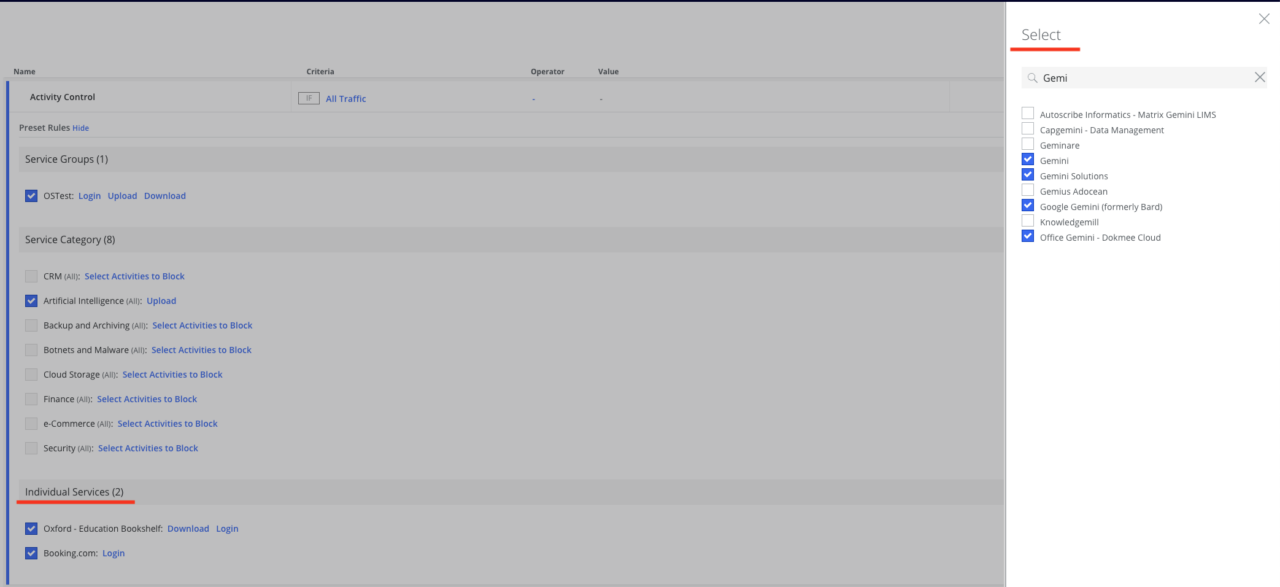
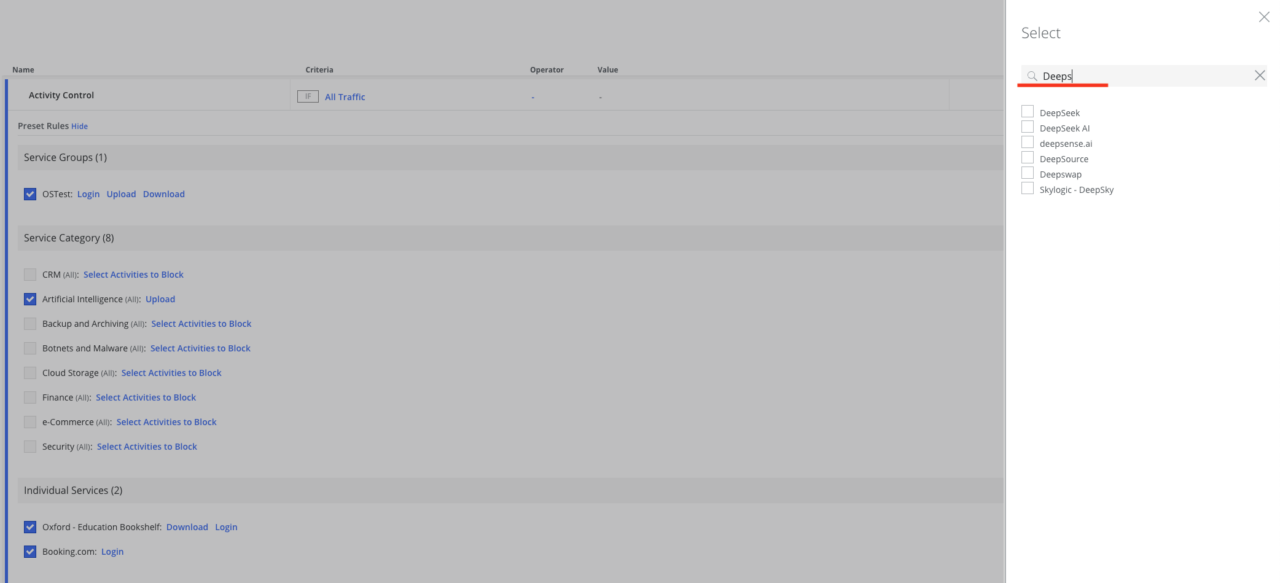
The Skyhigh Security vendor constantly updates the list of services and adds new ones—for example, the new DeepSeek language model is already available.
PA (Privilege Access)
The second option—the PA (Privilege Access) solution—works based on ZTNA technology, that is, zero-trust access. Its purpose is to grant access to legitimate services for specific users according to their role in the company. Control is provided, based on DLP policies that are specifically created and linked to rules.
That is how everything happens. The user enters the portal with a list of services to which he has access.
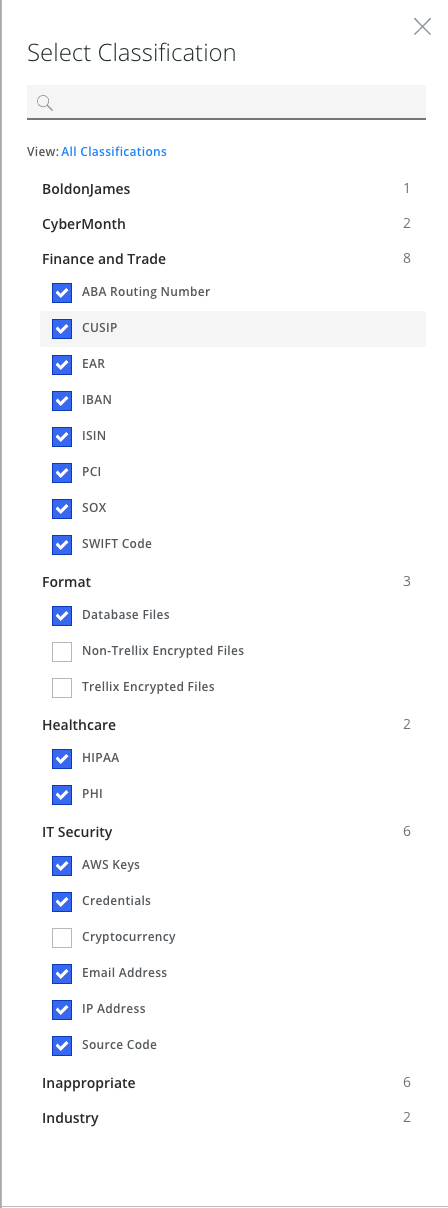
The administrator creates a rule to control the classification of the content shared by the user (in our case, it will be financial information).
![]()
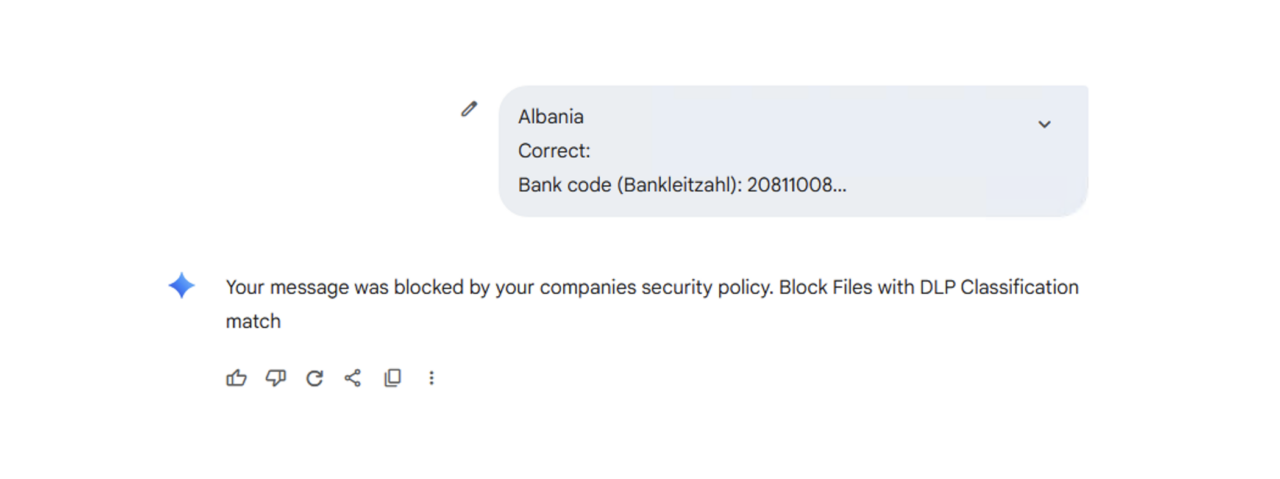
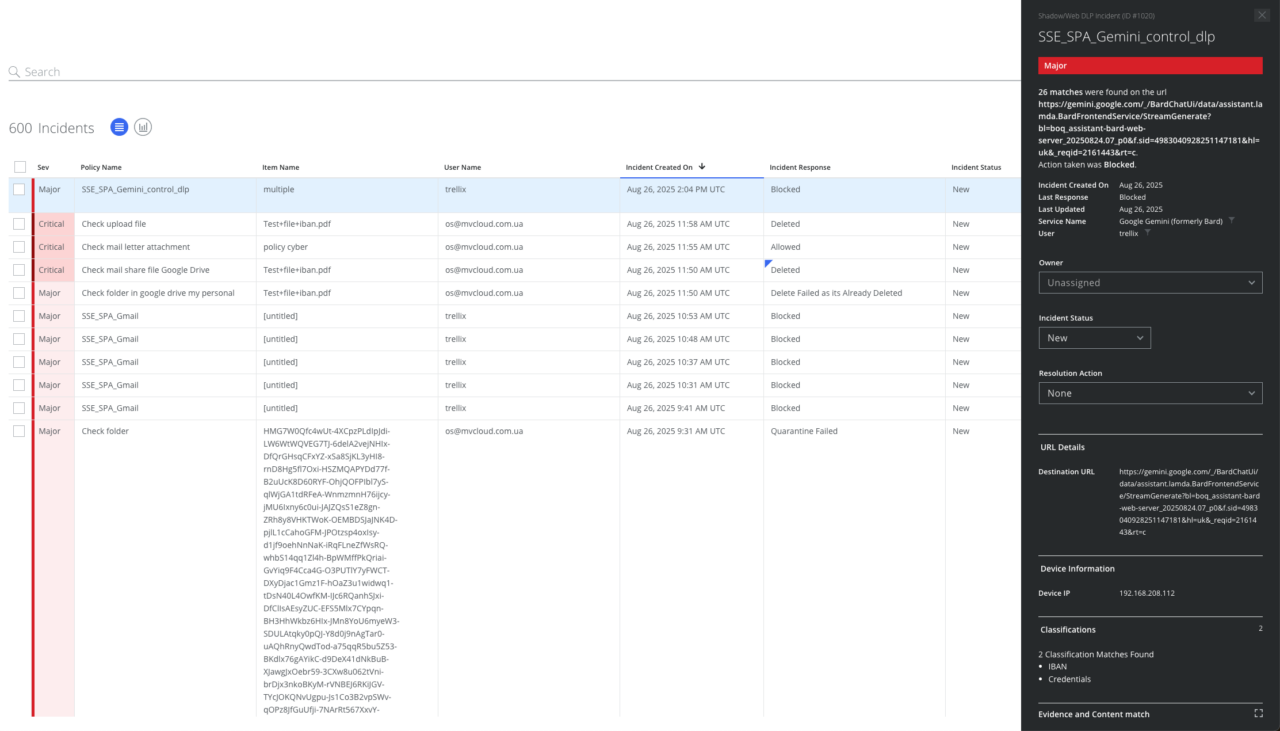
When a user attempts to submit information classified as financial, a rejection message is displayed, and the administrator sees a notification in the system that can be used for post-incident analysis.
Conclusion
Artificial intelligence is now a favorite tool of employees at many companies. Its convenience and apparent almightiness overshadow such an important aspect as data security. Users focus on getting results — that is, answers to their questions — unwittingly becoming a source of confidential information leaks.
To minimize risks, it is critical to develop internal policies on permitted AI services and control data sharing through DLP, SWG, and PA solutions. And, of course, to constantly update security rules in accordance with new services and market trends. By getting the technology and security policies right, you can take full advantage of AI without putting your company at risk.
If you want to know more about Skyhigh Security solutions, please contact us: [email protected]
 Austria
Austria  Azerbaijan
Azerbaijan  Bosnia and Herzegovina
Bosnia and Herzegovina  Bulgaria
Bulgaria  Croatia
Croatia  Czech Republic
Czech Republic  Denmark
Denmark  Estonia
Estonia  Finland
Finland  Georgia
Georgia  Germany
Germany  Hungary
Hungary  Kazakhstan
Kazakhstan  Kyrgyzstan
Kyrgyzstan  Latvia
Latvia  Lithuania
Lithuania  Moldova
Moldova  Montenegro
Montenegro  North Macedonia
North Macedonia  Norway
Norway  Poland
Poland  Romania
Romania  Serbia
Serbia  Slovakia
Slovakia  Slovenia
Slovenia  Sweden
Sweden  Switzerland
Switzerland  Tajikistan
Tajikistan  Turkmenistan
Turkmenistan  Ukraine
Ukraine  Uzbekistan
Uzbekistan 


