Brief overview of the UAC-0219 vulnerability
In the fall of 2024, the Ukrainian Government Computer Emergency Response Team (CERT-UA) discovered the UAC-0219 vulnerability, which is still active today. It was aimed at the public sector to obtain confidential information from users’ workstations.
The attack succeeded because it began with social engineering techniques. Victims received phishing emails containing malicious links or attachments that persuaded them to open them. According to CERT-UA, the links redirected users to compromised cloud services such as DropMeFiles, Google Drive, and others. In some cases, the attachment was a PDF file with a VBScript loader, which triggered the infection chain: downloading malware, executing PowerShell scripts to search for and upload files using cURL according to a list of extensions (“*.doc”, “*.txt”, “*.docx”, “*.xls”, “*.xlsx”, “*.pdf”, “*.rtf”, “*.odt”, “*.csv”, “*.ods”, “*.ppt”, “*.pptx”, “*.png”, “*.jpg”, “*.jpeg”), as well as taking screenshots of the computer.
Initially, the malicious group used EXE files created with the NSIS installer, which contained a decoy, although the main tool for file theft was WRECKSTEEL.
Today, the UAC-0219 vulnerability has become more difficult to detect without proper tools.
A full list of compromise indicators is published on CERT-UA.
Schematically, the attack looks like this:
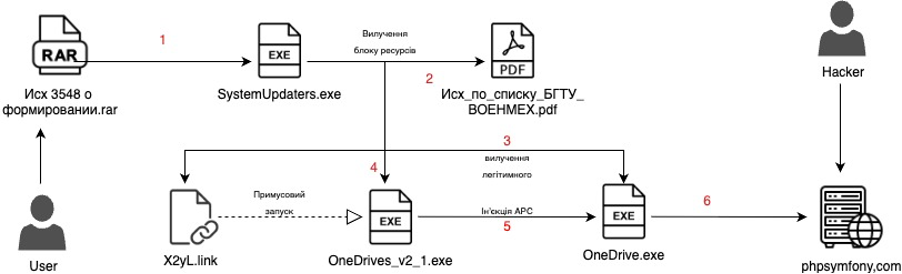
How the UAC-0219 threat could have been prevented or mitigated
For effective protection in this case, a combination of Skyhigh Security solutions could have been used: SWG (Secure Web Gateway), CASB (Cloud Access Security Broker), and DLP (Data Loss Prevention). The vendor’s products allow you to build an ecosystem that provides comprehensive protection and threat monitoring across the company’s infrastructure.
SWG – the first line of defense
Since the attack began with phishing emails and redirecting users via a link, the SWG (Secure Web Gateway) module could have been the first line of defense to minimize risks and absorb the initial impact.
The solution categorizes and assigns a risk score to the page during user interaction to prevent redirection to suspicious websites.
Below is a screenshot showing the configuration of a categorization policy set to block access to categorized sites:
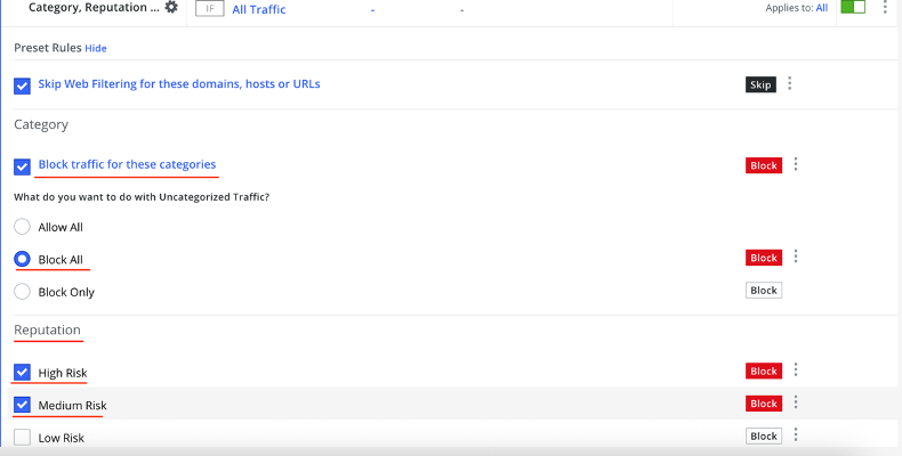
The list of categories is formed following the organization’s security policy and can include types of resources such as malicious, games, illegal, etc. In the next example, a separate category for phishing web pages is highlighted:
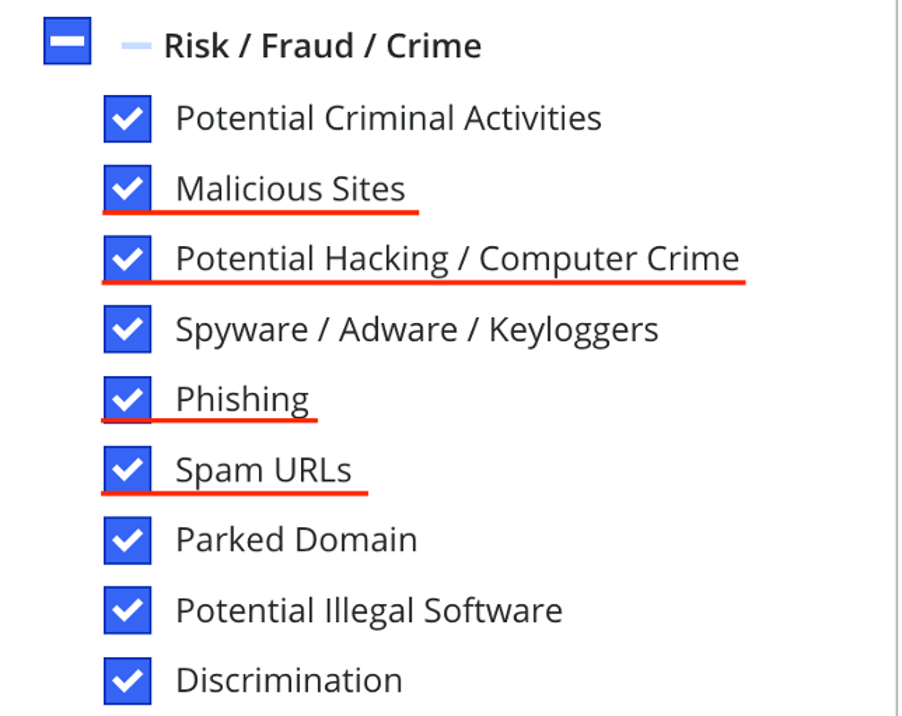
Web resources are also evaluated by reputation level, which helps reduce risks associated with malicious websites.
If necessary, additional policies can be configured to specifically block known vulnerabilities. This enables a rapid response to threats and helps maintain control over the situation.
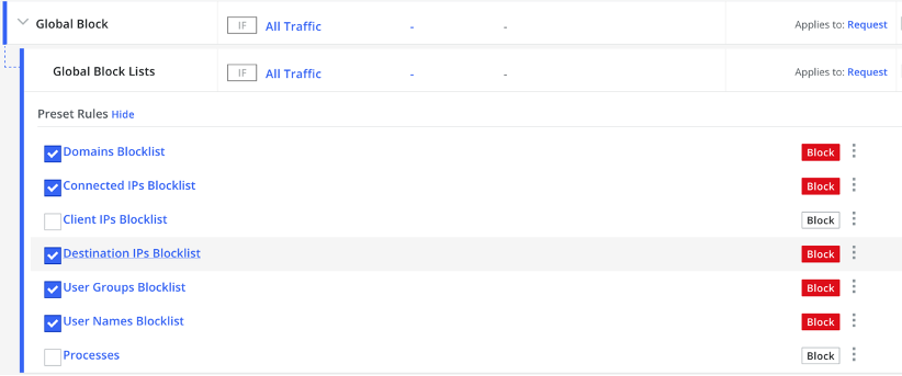
If the file format used to infect a workstation is known, its download can be blocked.
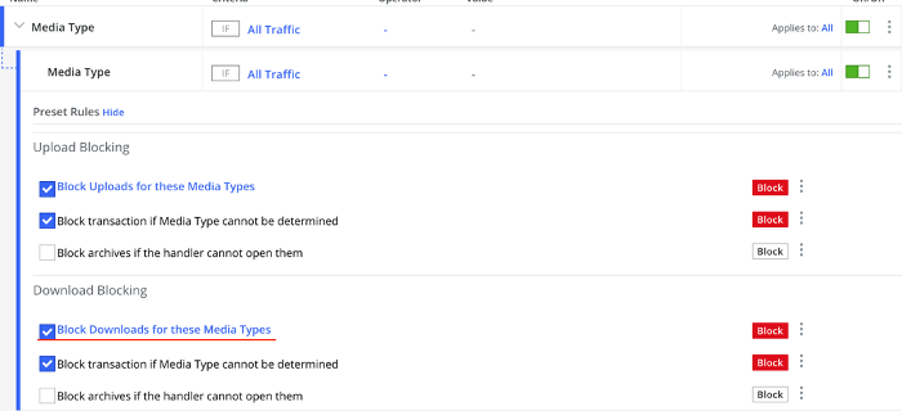
These are just some capabilities offered by the Secure Web Gateway solution, and the mentioned policies can effectively protect an organization from such attacks.
A Secure Web Gateway enforces configured rules and provides network traffic analytics from user workstations. This enables an information security specialist to detect and respond to abnormal activity.
Protection with Cloud Access Security Broker (CASB)
If an organization’s IT infrastructure operates in a cloud environment, such vulnerabilities also pose a risk. In this case, the Skyhigh Security CASB solution serves as an intermediate protective layer between the user and cloud services.
Data Loss Prevention (DLP)
If an attack has already occurred and an attacker attempts to transfer data from a workstation outside the company, a DLP solution can prevent this by enforcing policies that block the leakage of confidential information — regardless of how it is being transferred: via email, a link, or another method.
The images show examples of such policies. One policy monitors attempts to grant external users access to files via a link. If a file is automatically classified as containing financial information, the system records the incident and blocks access sharing.
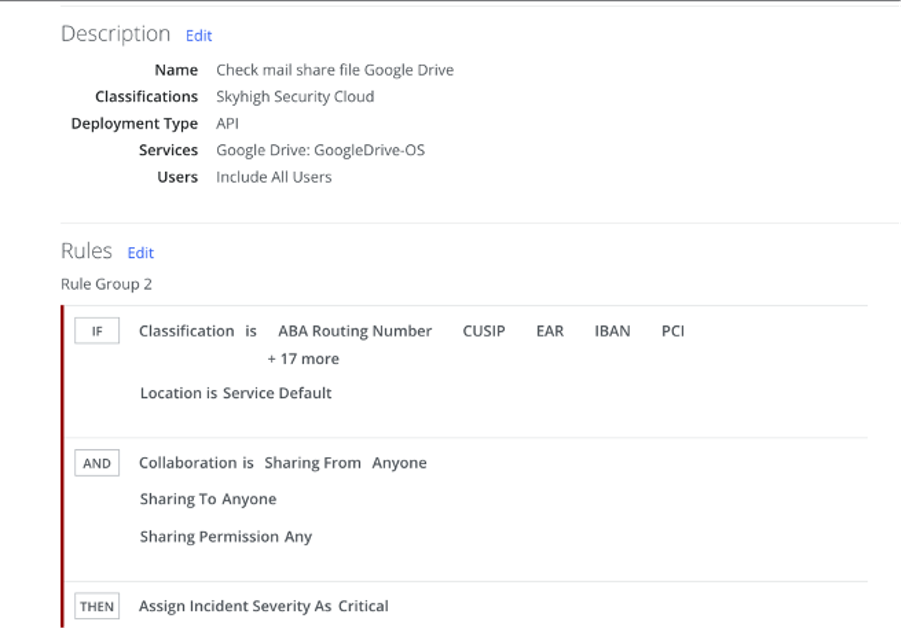
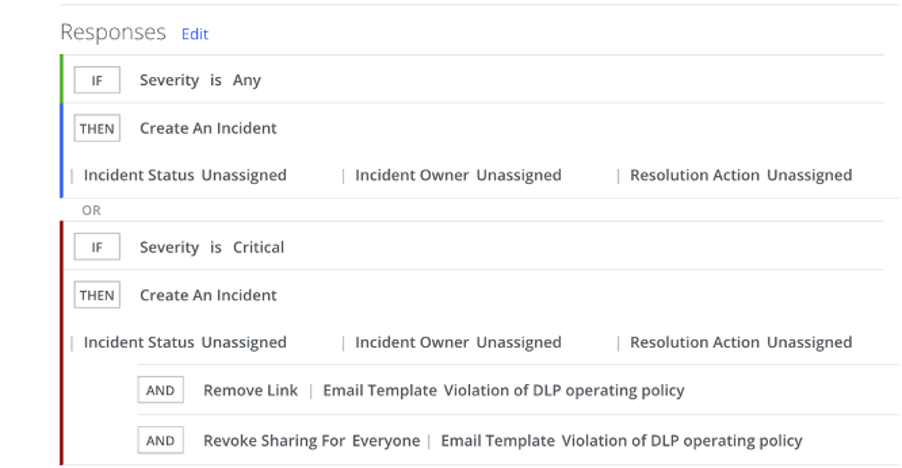
After a policy is triggered, post-incident analysis is carried out, which is critically important for further action.
As shown in the image below, the solution provides full incident details: which policy was triggered, which user initiated the event, and the compromise indicators that the rule responded to.
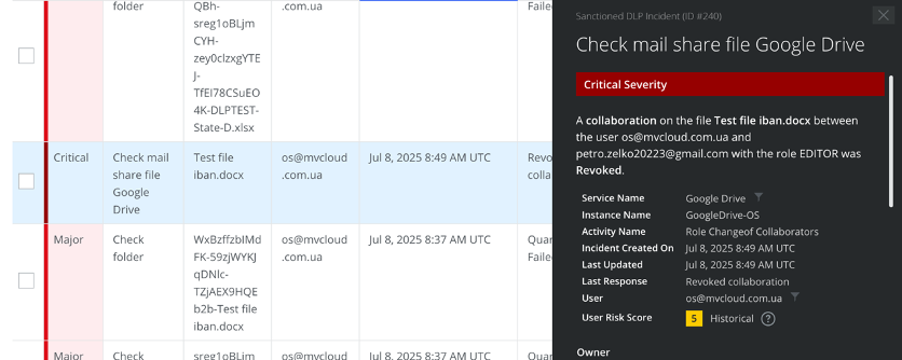
With Skyhigh Security, it is also possible to configure cloud infrastructure scans for malicious software and verify system configuration.
What’s next?
The primary task of an information security engineer is to reduce risks to an acceptable level or eliminate them. To achieve this, reliable, comprehensive protection and monitoring tools are needed, such as Skyhigh Security solutions.
Sign up for a consultation to learn how to integrate Skyhigh Security solutions into your project.
 Austria
Austria  Azerbaijan
Azerbaijan  Bosnia and Herzegovina
Bosnia and Herzegovina  Bulgaria
Bulgaria  Croatia
Croatia  Czech Republic
Czech Republic  Denmark
Denmark  Estonia
Estonia  Finland
Finland  Georgia
Georgia  Germany
Germany  Hungary
Hungary  Kazakhstan
Kazakhstan  Kyrgyzstan
Kyrgyzstan  Latvia
Latvia  Lithuania
Lithuania  Moldova
Moldova  Montenegro
Montenegro  North Macedonia
North Macedonia  Norway
Norway  Poland
Poland  Romania
Romania  Serbia
Serbia  Slovakia
Slovakia  Slovenia
Slovenia  Sweden
Sweden  Switzerland
Switzerland  Tajikistan
Tajikistan  Turkmenistan
Turkmenistan  Ukraine
Ukraine  Uzbekistan
Uzbekistan 


