Greetings everyone!
I’m Ivan Rudnytskyi , a Sales Engineer at BAKOTECH. Let me clarify for those who might be unaware, a Sales Engineer is not the same as a Sales Manager. A Sales Engineer is a technical engineer with sales expertise. I have more than 15 years of experience as an IT engineer, specializing primarily in web application security.
In my role, I frequently encounter client requests that seem straightforward, like “We need protection against DDoS attacks.” However, there are numerous nuances involved, leading to a barrage of questions.
What type of DDoS attack protection is required?
For which infrastructure? On-premises or cloud-based?
What are the specific business needs of the client company?
Certainly, there are multiple approaches to deploying anti-DDoS and intrusion prevention solutions, each with its own set of pros and cons. This article will delve into these aspects.
But first let’s explore some analytics.
According to statistics, DDoS attacks are one of the most common cybersecurity threats facing organizations today. With the beginning of a full-scale war, Ukraine took first place by the number of DDoS attacks. In just 9 months, the total number of attacks crossed the mark of 1,200,000.
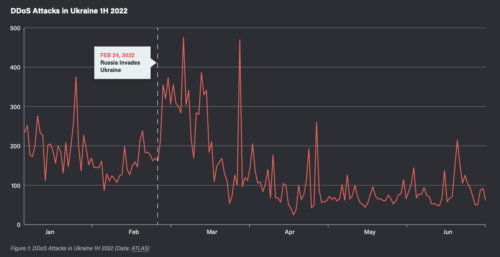
Between 2005 and 2013, the global incidence of DDoS attacks skyrocketed from hundreds to thousands, and today, the number of attacks reaches into the millions annually. With each passing year, the sophistication of DDoS attacks continues to escalate, as threat actors devise new methods to bypass cybersecurity defenses and circumvent traditional mitigation strategies.
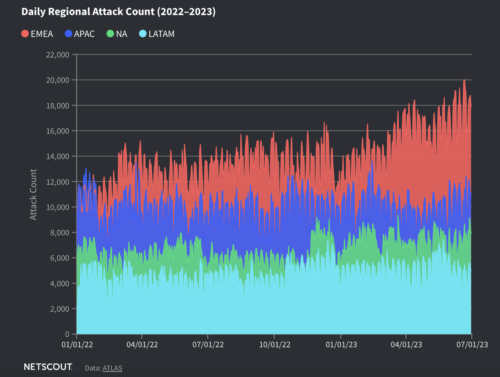
So, how to organize effective protection against DDoS attacks and minimize their negative impact on work processes? Let’s figure it out.
This article will cover:
- Requirements for a modern anti-DDoS system
- Ways to implement security components
- Approaches to solution architecture for DDoS protection
– Traditional method
– Cloud DDoS protection service
– DDoS protection service by a telecommunications operator
– Hybrid solutions - A comprehensive approach to the deployment of countermeasures against attacks and intrusions
- Conclusions
Requirements for a modern anti-DDoS system
The system should provide automated counteraction against DDoS attacks on network infrastructure and applications at layers 2-7 of the OSI model.
These systems are architecturally composed of the following components:
- Hardware and software complex for automatic DDoS attack protection (traffic cleaning) that combines several levels of protection and uses specialized software and hardware components designed to combat powerful flood attacks. If the existing bandwidth of the current data center is insufficient to filter broadband DDoS attacks, attack filtering should be based on an external (for example, a service provider solution) or cloud service. In this situation, traffic can be automatically or manually redirected to external cleaning centers, thus minimizing the impact of the attack on the data center’s communication channel.
- Web Application Firewall (WAF) – a system designed to automatically combat specific attacks targeting web applications, as well as slowloris attacks on them.
- Solution support service – a highly desirable, non-technical, organizational component that provides assistance with filtering and/or configuration. It would be perfect if it is available 24/7/365.
Ways to implement security components
It is recommended to install the hardware and software complex in the network gap (inline) — on the route of traffic movement. Deploying the hardware and software complex inline, within the network traffic path, is considered an effective approach for DDoS mitigation.
However, inline deployment introduces a potential risk of complete traffic disruption in case of a protection component failure. Therefore, it is crucial to ensure solution redundancy and implement traffic bypass capabilities to allow unfiltered traffic flow in case of the filtering device’s malfunction.
Inline deployment helps you achieve two positive points at once:
1) real-time inspection of all traffic, not just a subset, ensuring thorough protection,
2) protection of all company infrastructure components from both external and internal DDoS attacks
Outgoing traffic is also checked, which is an essential security measure.
It is worth considering that since both routers and firewalls often use external “white” IP addresses, this makes them potential attack targets. Attackers can easily obtain this information, enabling them to identify open ports, operating system versions, and system services. By exploiting known TCP/IP stack vulnerabilities, they can launch attacks against the system itself.
In this case, inline deployment of the protection system effectively addresses these concerns by enabling the detection and mitigation of such attacks, safeguarding the entire infrastructure.
Approaches to solution architecture for DDoS protection
Let’s look at the four main approaches, considering their pros and cons.
Traditional method
A traditional method of DDoS attack protection is implementation of a specialized On-Premise solution within the data center network. The primary and sole function of this solution is to filter malicious traffic.
Key Advantages:
- Complete user traffic control, the fine-tuning by the department of informationnetwork technologies.
- Sensitive data, such as encryption keys or encrypted session content, remains confidential within the organization, avoiding disclosure to third parties.
Key Disadvantages:
- The need for a dedicated support team with in-depth DDoS expertise, regular training, and 24/7/365 availability.
- A high-bandwidth Internet connection is required. On-Premise solutions may be ineffective against attacks if the connection between the solution and the ISP becomes saturated with malicious traffic.
Timely updates of the signatures and software of On-Premise solutions are crucial to keep them up-to-date.
Cloud DDoS protection service
In the face of the ease with which massive DDoS attacks can be launched, protecting communication channels becomes a critical concern. Cloud-based DDoS mitigation services address this challenge by offering cloud-based protection technologies, utilizing a remote and typically topologically distributed network.
Key Advantages:
- Rapid implementation.
- Quick adaptation to diverse attacks
- Expert support which relieves the customer of the need to independently train employees
Key Disadvantages:
- Cloud-based solutions require rerouting traffic through the cloud, either continuously or only under attack. Continuous rerouting can impact traffic statistics, incident response times, filtered attacks, and filtration accuracy.
- Dependency on Cloud Network Architecture. The company providing the cloud solution must ensure that its network meets the current level of threats at any given time.
DDoS protection service by a telecommunications operator
This is a special case of a cloud solution. Many internet service providers (ISP) additionally offer an anti-DDoS service based on their equipment. While similar to cloud-based solutions, they eliminate the need for separate traffic rerouting since traffic already passes through the provider’s equipment.
Despite the obvious advantages of this approach, there are a number of disadvantages, the most critical of which is the absence (in most cases) of guarantees that the ISP can handle the DDoS attack on its own. If not, this can lead to the unavailability of the protected service.
Therefore, I do not recommend choosing the “DDoS protection” service provided by the ISP as the sole security measure. It is highly desirable to use it together with an On-Premise, cloud-based, or hybrid solution (provided that the provider, if unable to cope with the DDoS attack, allows some of the malicious traffic to pass through).
Hybrid solutions: an approach that allows you to successfully counter DDoS in large organizations
The hybrid approach to DDoS mitigation combines On-Premise and cloud-based/provider solutions to compensate for the individual drawbacks of each solution.
In this approach, the two solutions are used in parallel. The On-Premise solution is used for continuous protection against application-layer attacks, while the cloud-based solution is designed to filter all other attacks and can operate in both always-on and on-demand modes.
Key Advantages:
- Reduced reliance on the cloud network
- Ability to filter a range of application-layer attacks without delay
- Enhanced solution reliability
Key Disadvantages:
- Attack response time and potential delays during switching — the protected resource may be temporarily unavailable
- Increased costs (in terms of man-hours) to implement essentially two parallel solutions for the same task
So, each of the discussed approaches has its own set of pros and cons. Relying solely on one approach may leave vulnerabilities in your defense. Therefore, I suggest focusing on the strengths of each solution by combining them into an even more powerful protection strategy. Imagine the listed approaches to anti-DDoS solution architecture as the Avengers, powerful individually but nearly unstoppable together.
What do we see?
A comprehensive approach to the deployment of countermeasures against attacks and intrusions
To protect against modern attacks, regardless of the chosen solution architecture, a comprehensive approach to security construction should be followed.
A network attack protection solution, designed to exhaust the resources of servers and network equipment, should be placed in front of the company’s data center border router, thereby protecting the entire company’s infrastructure from attacks of this class.
Note that this approach helps protect not only data center servers, but also the border firewall. If you are using an external or cloud solution, this requirement is automatically met.
A web application firewall (WAF) solution should be installed after the network attack protection module.
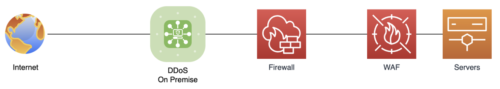
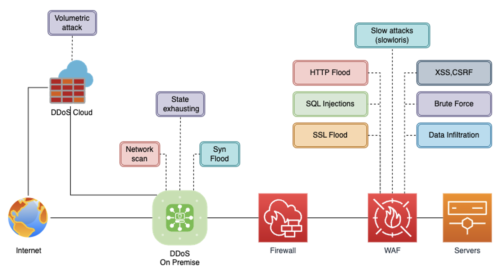
Such an architecture will effectively counter almost all known attacks. Structurally, the system of complex countermeasures can look, for example, as in the figure below. It also shows the components of the solution that protect against typical attacks, namely:
- DdoS Cloud protection – a cloud solution for protection against DDoS attacks;
- DdoS On-premise – a solution in the client’s infrastructure;
- WAF – a solution that provides DDoS protection at the application level.
Conclusions
DDoS remains a burning issue and is not going to die out – attackers do not stop modernizing their tactics and methods to carry out hybrid DDoS attacks, and their volumes continue to grow. That is why companies should consider new ways to protect against DDoS in order to effectively counteract the growing complexity of these attacks.
However, in fairness, I must note that I quite often come across the fact that companies think about DDoS protection last of all – “no DDoS, no problem.” But when hackers start to attack, it’s too late. This is a common trend in both Ukrainian and foreign companies. And unfortunately, not all companies yet consciously approach the risk of DDoS attacks and possible financial and reputational losses as a result.
 Austria
Austria  Azerbaijan
Azerbaijan  Bosnia and Herzegovina
Bosnia and Herzegovina  Bulgaria
Bulgaria  Croatia
Croatia  Czech Republic
Czech Republic  Denmark
Denmark  Estonia
Estonia  Finland
Finland  Georgia
Georgia  Germany
Germany  Hungary
Hungary  Kazakhstan
Kazakhstan  Kyrgyzstan
Kyrgyzstan  Latvia
Latvia  Lithuania
Lithuania  Moldova
Moldova  Montenegro
Montenegro  North Macedonia
North Macedonia  Norway
Norway  Poland
Poland  Romania
Romania  Serbia
Serbia  Slovakia
Slovakia  Slovenia
Slovenia  Sweden
Sweden  Switzerland
Switzerland  Tajikistan
Tajikistan  Turkmenistan
Turkmenistan  Ukraine
Ukraine  Uzbekistan
Uzbekistan